By: Sarah Goltz, Content Manager on February 14th, 2022
4 ways a cybersecurity incident can hurt your business
As technology becomes more advanced, cyber hackers are utilizing new tactics to infiltrate your network. It seems like every day there is a new headline about a business dealing with the consequences of a new cyber threat.
Cybersecurity is the only barrier between your business's confidential information and a hacker. Questioning the need for cybersecurity can be viewed as questioning the reason for locks on your house. They're there to keep you safe. The more security you have on your home, the less likely a burglar would want to target you. They want to go to the houses that will be easy to break into.
Whether your business is small, medium, or large, size does not make a difference when it comes to cyber incidents. All companies have what a hacker is looking for sensitive information and money. Regardless of your size, they will target you to get these two things.
You may be wondering what the actual costs of a cybersecurity incident are. What kind of damage can they cause my company? As a managed service provider, we have a strong sense of the long and short-term damage attacks can cause companies because they often turn to us after the event to ensure it never happens again.
Here are some of the 4 most significant ways a cybersecurity incident can hurt your business if you don’t maintain a secure environment.
1. Damaged reputation
Having a scathed reputation can have a very negative impact on your business. The risk of having a cyber attack will not only affect your business physically, but it will also affect your reputation. When you undergo a cyber attack, many businesses will know that you are not secure.
Clients may not want to work with you because they don't trust you can keep their credentials and data safe. Reputation damage can affect your business in several ways, such as:
- Loss of customers
- Fall in sales
- Decrease in employee retention
- Difficulty hiring & increased hiring costs
It can be tough to earn back the trust of other businesses and clients after you have a breach. The best way to maintain a good reputation is to ensure you use all the necessary resources to create a secure and reliable IT environment.
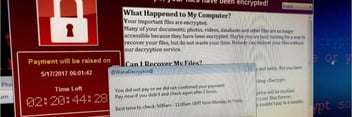
2. Ransomware
Leaving yourself unarmed from a cyber attack dramatically increases your risk of a ransomware attack. Ransomware is a form of malicious software that encrypts your computer system and blocks access to valuable information or files until a certain amount of money is paid to the ransomware hacker.
Getting hit by a ransomware attack can happen to any person or business, small, medium, or large. Once they have gotten ahold of your system, it can result in a significant loss of money and time until the system is back up and running properly.
3. Downtime
We have all heard the phrase, “time is money.” Well, in the situation that your business is hit with a cyber attack, that usually is the case. When a cybersecurity incident takes place, it is unlikely there won’t be downtime. The worse the incident, the more downtime you can expect to get your systems up and running.
Waiting to get a cyber attack resolved will make it very hard for your business to continue working. This can cause you to miss profitable opportunities and lose money from clients if you cannot provide your services to them.
Depending on the severity, your clients may not want to continue working with you for fear that an event like this could occur again. The best way to reduce downtime is to have a disaster recovery plan in place.
A disaster recovery plan is a process that is designed to assist an organization in executing recovery in response to a cyber attack. This plan will consist of the action that needs to be taken before, during, and after a cyber attack.
Having a process in place is meant to reduce the amount of downtime so that your business can get back to providing its services and focusing on its mission.
4. Loss of intellectual property
There is nothing more terrifying than all of your confidential data and information getting in the hands of a malicious hacker. Hackers have a few options for what they will do with your intellectual property.
They can steal your information and sell it to another company for money. Another common tactic is hackers holding your intellectual property for ransom until you pay them the demanded amount of money.
The issue with paying the hacker's monetary demand is that the hacker very likely could have made a copy of the document before giving it back to you. There's no way to completely confirm that your intellectual property is safe and won't get into more people's hands.
For this reason, it is important to have layers of security to notify you when suspicious activity is taking place on your network. Utilizing the right tools can make it much more difficult for hackers to get their hands on confidential information.
Your business can become uninsurable
Many cyber insurance companies have a set of cybersecurity tools and processes that must be followed to insure you. Insurance companies don't want to insure a company with no cybersecurity processes and tools in place.
For insurance companies, you would be a significant liability and would likely end up costing them more than your business is worth. For this reason, if you are a business that doesnt have the proper security processes in place and overlook cyber threats, it is unlikely you’ll find an insurance company that will support you.
In the event of a cyber attack, not having cyber insurance could end up costing you a great deal of money. Suppose you are considered uninsurable by a cyber insurance company. In that case, this is a good sign you need to make some changes to your current cybersecurity plan because you are likely at a high risk of cyber threats.
How to mitigate the risk of cybersecurity incidents:
The only way to prevent becoming a victim of a cyber threat is to be proactive with advanced cyber security technology and monitoring. It doesnt matter the size, industry, or location of your company. If you don’t have a sound cybersecurity system to make it difficult for a hacker to infiltrate, you will become an easy target.
To enhance cybersecurity, many companies turn to a managed service provider. A managed service provider will work with you to create a secure and optimized IT environment.
As a managed service provider, Usherwood supports companies with unique standards to help ensure that their environment remains secure. Usherwood places a strong emphasis on cybersecurity. Our goal is to understand your environment and implement the tools necessary to monitor and protect your network from malicious threats.
Wondering how much you should invest into your cybersecurity? Check out this article: How Much Should You Spend on Cybersecurity? (Budget, Costs).
Read On

Why Small Businesses Are a Target for Cyber Threats and How MSPs Can Help
When you think about hacking and who is typically the target, it is often associated with large...

How much should you spend on cybersecurity? (Budget, costs)
Whether or not you want to invest in cybersecurity, it isn’t an option anymore. Cyber threats are...
The Dangers of Ransomware to Your Business
Ransomware victims can vary from large global companies to small businesses. Every business should...



